When I started out, I was terribly confused about OpenID. It's actually really simple and straightforward. Hopefully this guide helps.
Getting an OpenID username and password
The first step was to get myself an OpenID account. This part confused me to start with because I assumed that there would be one centralised OpenID provider. Not so! OpenID is completely decentralised which means that there are a number of OpenID providers. You can create an OpenID account with any of them. After some poking around, I decided to create an account with claimID. You'll be asked to set a username and password for your account, and in a couple of minutes the account will be ready. Along with the account, you'll get a page that you can fill with links. Mine is here. The important part though is in the page source. Do a View Source on that page, and you get these headers:
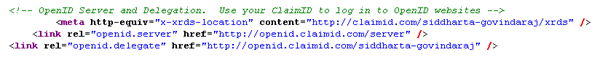
We'll see how these headers are used later on.
Logging into an OpenID enabled site
Right, so we've got an OpenID login. How do we use this to login to an OpenID enabled website? Lets go through an example. We are going to use OpenID to log into Ma.gnolia. First, go to the site and select the option to login with OpenID. You will be asked to enter your OpenID URL. Thats right, you don't enter your user name and password here. Instead you enter a URL. In this case, thats the claimID URL that we saw before. Enter that URL as shown below and click the Login button.
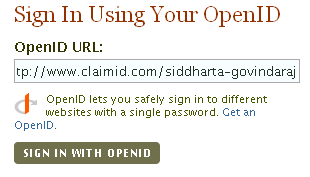
What Magnolia does is it retrieves the URL provided and reads the OpenID headers contained in it. Here it is again

The openid.server and openid.delegate fields tell the website which server to contact to handle the login. Magnolia then takes these bits of information and asks the server mentioned in the header to log in. You'll now be redirected to the login page on the OpenID server, where you'll be asked for a username and password. Enter the username and password that you set while creating your claimID account and click the Login button. The OpenID server will now verify your credentials and log you in. In this case, Mag.nolia is asking for some more information.
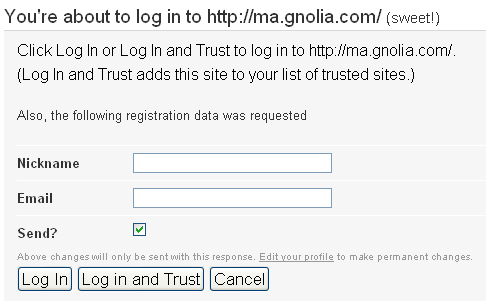
Fill up the form and you're done. There are two ways of logging in. "Log In" will just log you in normally, but will ask you for confirmation everytime you log in to the site. "Log In and Trust" will log you in and not ask for confirmation in the future. In any case, you can always change the settings later. Once you login, you'll be redirected back to the Ma.gnolia website to continue what you were doing. In the whole transaction, Ma.gnolia never finds out what your user name and password was. All they know is that the OpenID URL was validated correctly by the backend server.
Logging into another site
Let try it once more by logging into livejournal. First, select the option to login with OpenID.
Next, enter your OpenID URL as before.
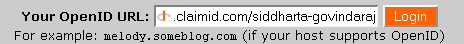
As before, livejournal contacts the OpenID server, but as we are already logged into that server, it doesn't ask us for entering the username and password again (Had you logged out of the OpenID server, it would have asked for the user name and password). Instead it jumps straight to the Log In confirmation screen. Click Log In and you're in. No account creation required! Pretty cool. All you need to remember is one user name and password and the URL to the page containing the OpenID headers.
OpenID delegation
Right, so you've got OpenID accounts at a number of sites, and one day claimID goes out of business. Have you lost all your login details at every website? Thats a scary thought. Luckily its all been taken care of. Enter OpenID delegation. Remember, you log into websites by entering a URL. The only purpose of that URL is to retrieve the OpenID headers. So, if you can create a page with the relevant OpenID headers, you can use that page as your OpenID login URL. Now, what I've done is to modify the blog template to add the OpenID headers to this page. Do a View Source on this blog, and you'll find these lines
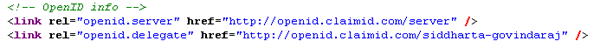
If you're using claimID, you dont even need to figure out the code because they conveniently provide you with the code snippet to paste into your own blog or website. I can now login using my blog address as the OpenID URL.
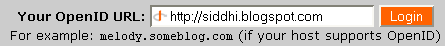
Lets say I create accounts on websites using this URL. As far as the website is concerned, it is the OpenID URL which is your identifier, not the backend details. So if claimID were to go out of business, or for any reason I wanted to switch, all I need to do is create an OpenID account at another provider and change the headers on this page to point to the new provider's details. When I login at a website, the website will now contact the new backend provider to log me in. My login URL at the website remains unchanged! Neat!
Security with OpenIDs
One of the big misconceptions that I had was that OpenID was a centralised system for authentication around the web (remember Microsoft Passport? Google is getting there too). It always scared me that if one account got compromised and someone figured out the username and password, it put all the other websites at risk. Nothing of the sort.
One thing to point out. Login details are stored on the backend OpenID server. The websites never get to know it. Even if a website gets compromised, cracked, whatever, and data gets stolen, your login details are safe. So OpenID is actually quite a bit safer in that respect.
Still, your login details may get compromised by any number of other means. Here are some things you can do to make it more secure.
First, OpenID delegation is a great thing, so set it up ASAP. If your user name and password were to get compromised, all you need to do is to create a new account with claimID (or any provider) and setup the delegation to the new account. The next time anyone uses your URL to log in, they will need to enter the NEW user name and password. Cool!
Second, nothing stops you from creating two or three OpenID accounts. You can then use one for say, all the social networking sites, another for your blogs and so on. If one were to get compromised, damage is only restricted to the sites that share the same OpenID account.
Conclusion
OpenID is pretty cool. It's becoming big. Get yourself an account and start playing around with it. Run a website? Think about supporting OpenID logins.
I've only been using OpenID for a couple of days, so if you have any feedback, comments or corrections, I would love to hear it.
8 comments:
In order for authorization to be supported, the folks in the OpenID community would need to have the desire of moving past the basics of identity. Likewise, the features of an identity selector (e.g. Cardspace) will need to change. IMHO it seems no one really cares to talk deeper about authorization as it may require too much work on their parts...
Hi James thanks for your comments.
I guess there is still a lot of work to be done on authorization and other identity issues.
However, for the use case of providing an authentication mechanism and enabling single sign on across websites, OpenID provides a reasonable working solution thats usable today.
That may not be as exciting as the other things that are being debated in the identity space (which, to be honest, I'm only just learning about) but it's still useful enough for people to start getting involved as users.
What if the blogspot goes out of business? You will have to change the URL that day. :-) Just kidding.
Jokes apart, this is nothing different from an LDAP server found in current IT environments. Kerberos is also something similar, but more secure, IMO. OpenID seems to be a new name to promote new business.
Also, this suffers from all the classic engineering problems - single thing is a bottleneck and insecure, multiple things are difficult to remember and manage etc.
@Anonymous:
The difference with OpenID and corporate LDAP server or MS Passport is that You as user choose identity provider (You chose Your OpenID URL) thus is not centralized like former solutions.
So it is less vulnerable to bottlenecks. Of course performance problems in one identity provider are common to all users using this provider, but not for all OpenID users.
So, if I "login and trust" does that mean that someone else can log in as me just by entering my openID url?
Or is there still a cookie that prevents it? If there isn't a cookie, how is it prevented?
@anonymous: If blogspot goes out of business you're screwed :p One of the things that is done is to put it on your own website (i.e website hosted by you)
@jim: Thats right, the OpenID server sets a cookie. The spec doesn't say anything about this. The server can use any method of authenticating, cookie is one way, the other ways are checking the IP address, or requesting the browser for a digital certificate and so on.
In fact, there are groups that want to make all authentication certificate based instead of username/password forms. That way a lot of phishing problems go away.
I want to ask a question..I want my website has a login bar with openID like livejournal website. How could I do it?Is anyone has a source about it? I would be glad if you help..thanks
@anonymous: There are some openid libraries which you can use to implement it. A list is available here - http://wiki.openid.net/Libraries
If you are using a common app like wordpress, there are openid plugins available that will do it for you
Post a Comment